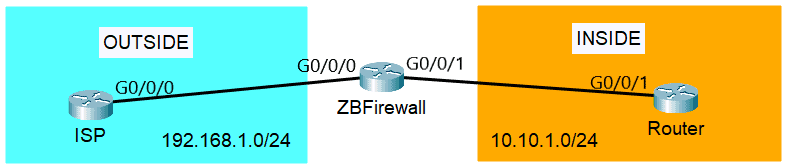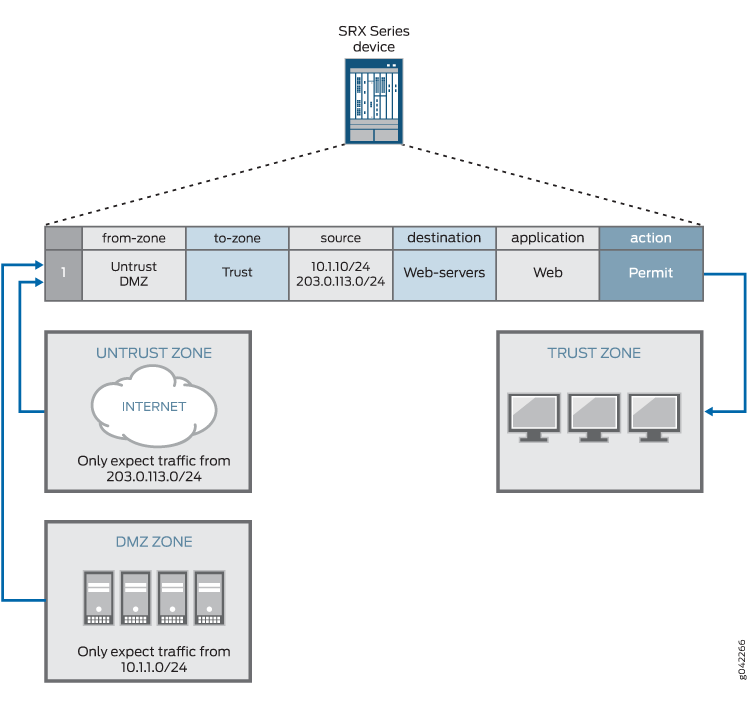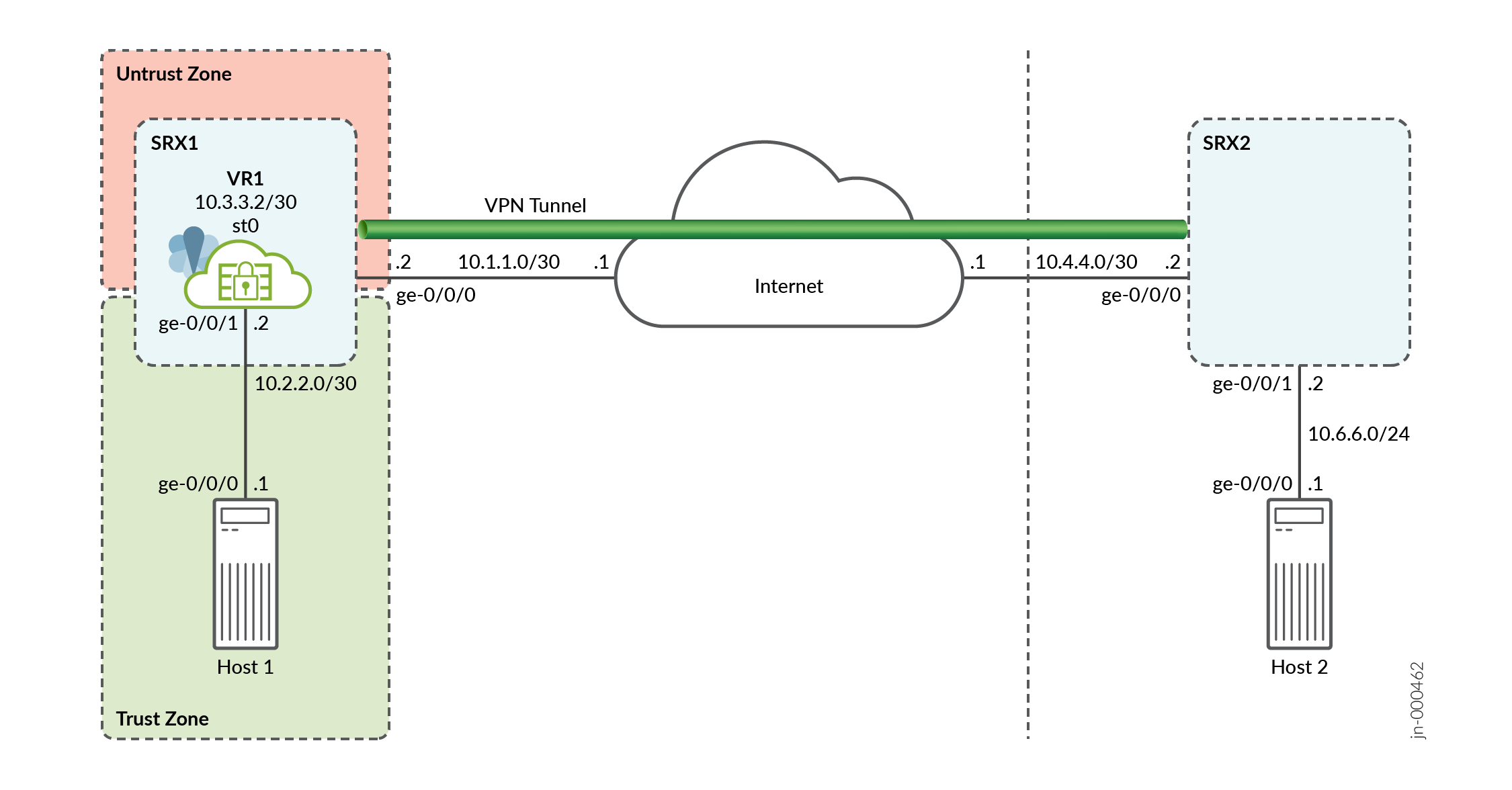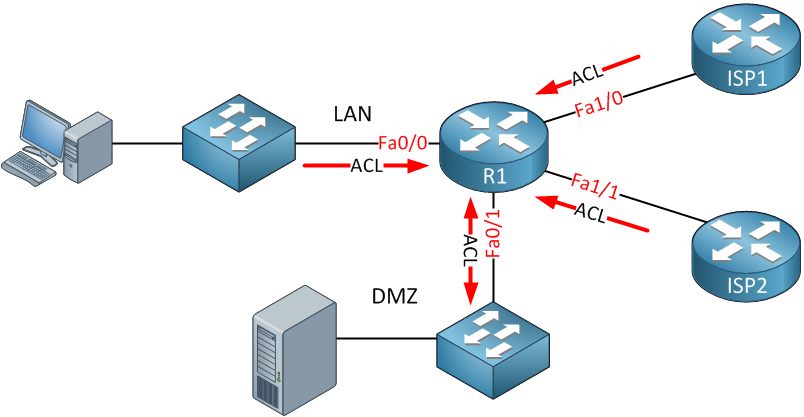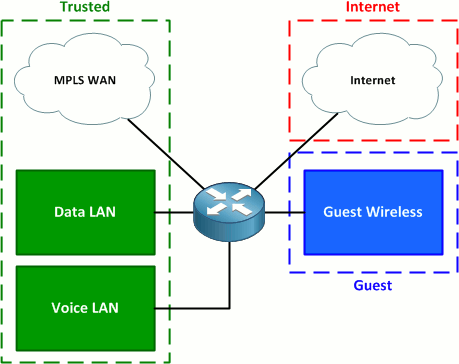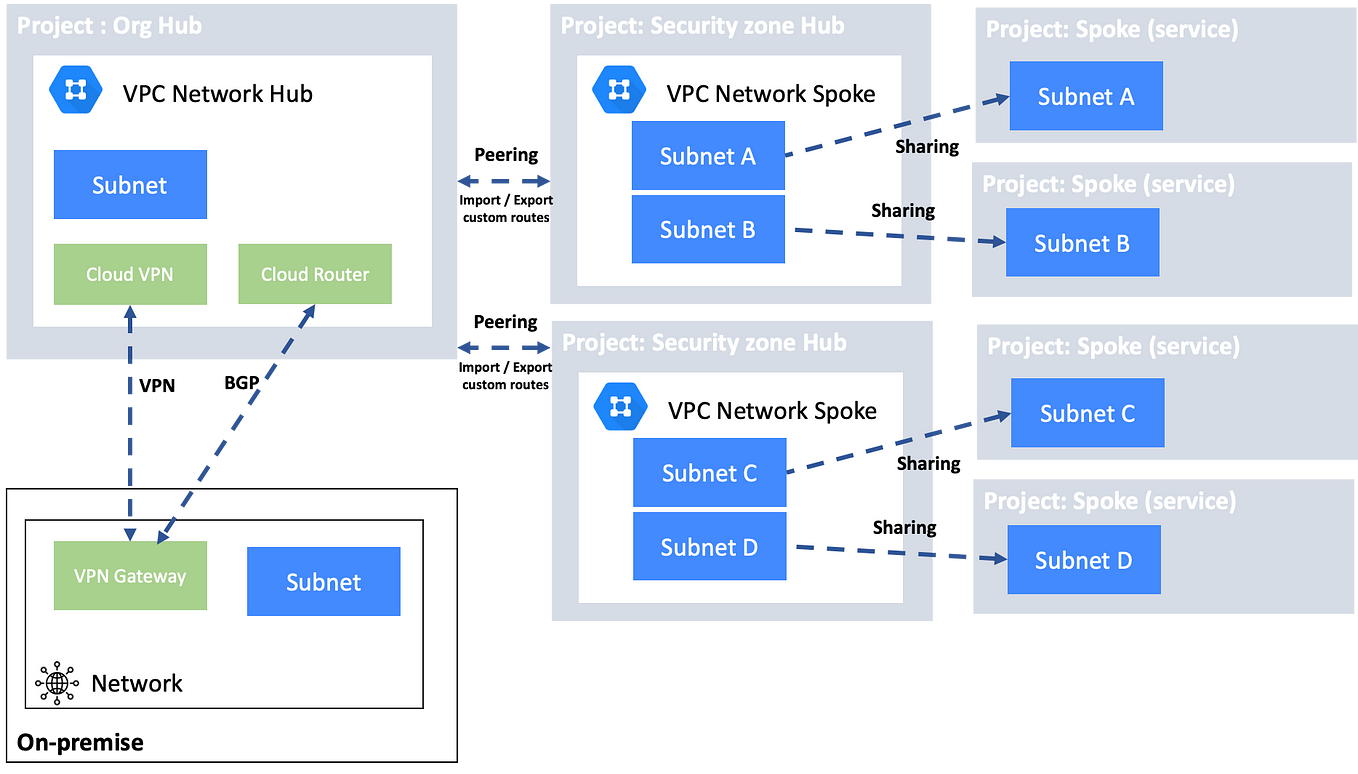
Simple Hybrid Hub-Spoke Network Topology on Google Cloud Platform (GCP) | by Hassene BELGACEM | Google Cloud - Community | Medium
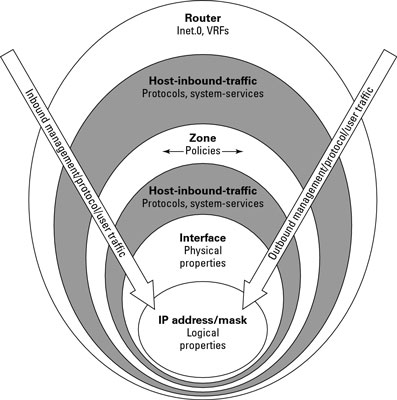
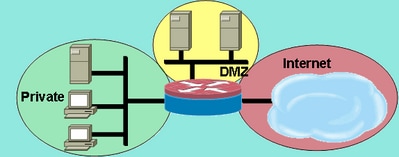
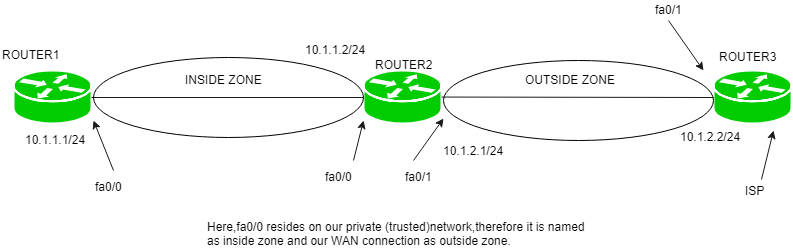
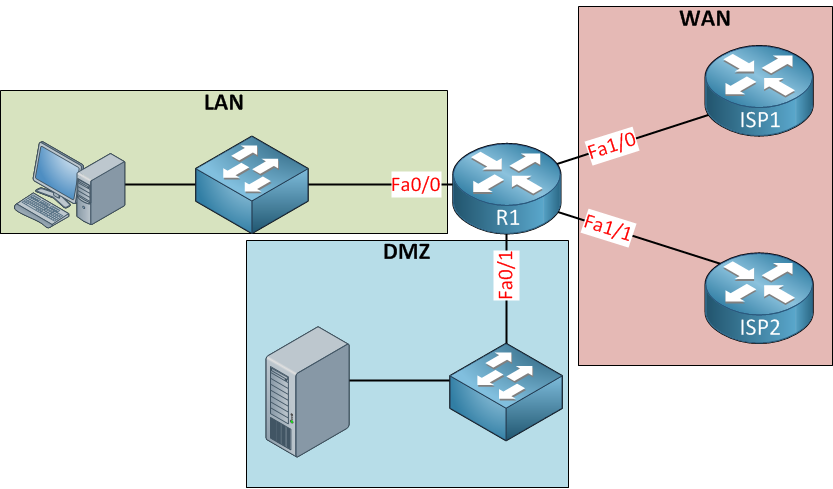
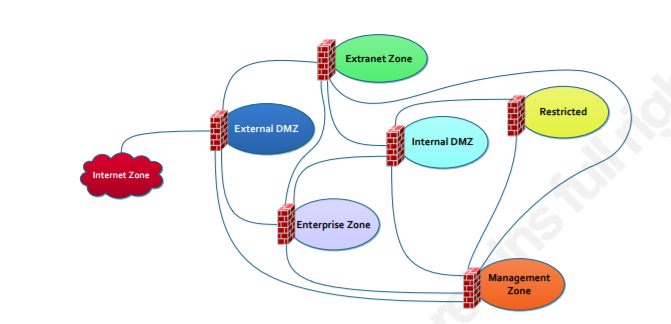
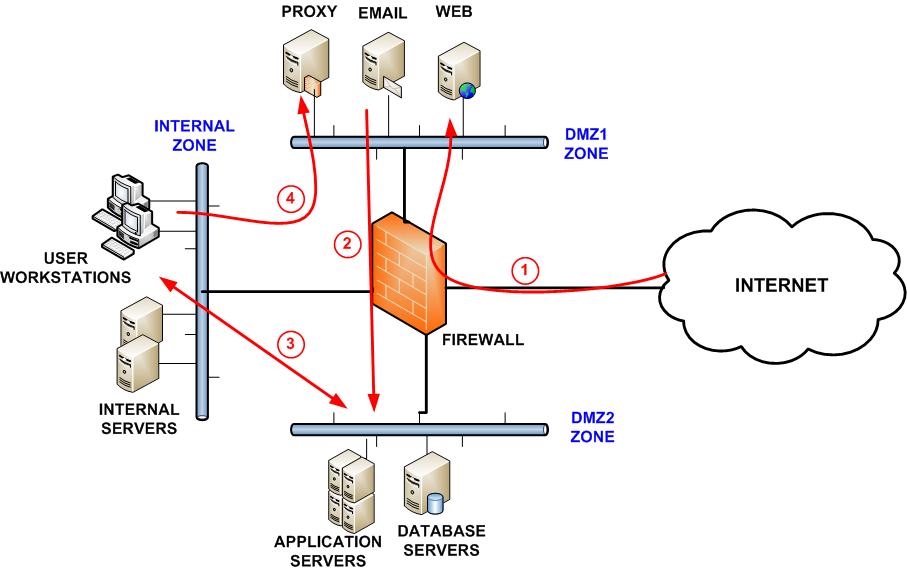
Baseline security requirements for network security zones (version 2.0) - ITSP.80.022 - Canadian Centre for Cyber Security