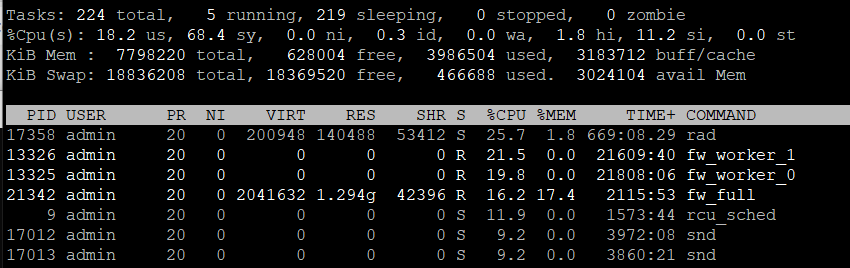
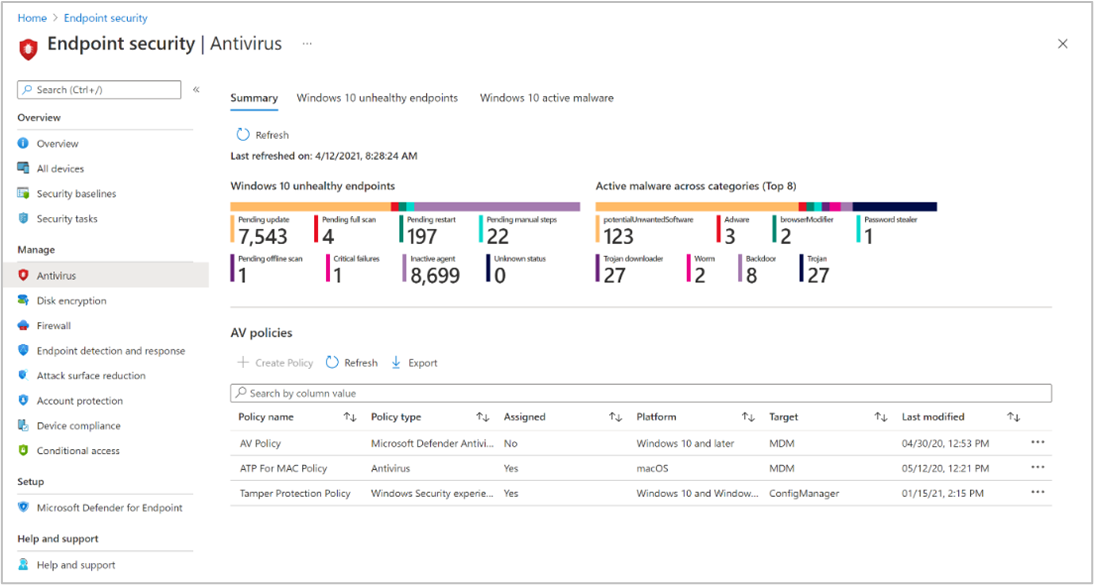
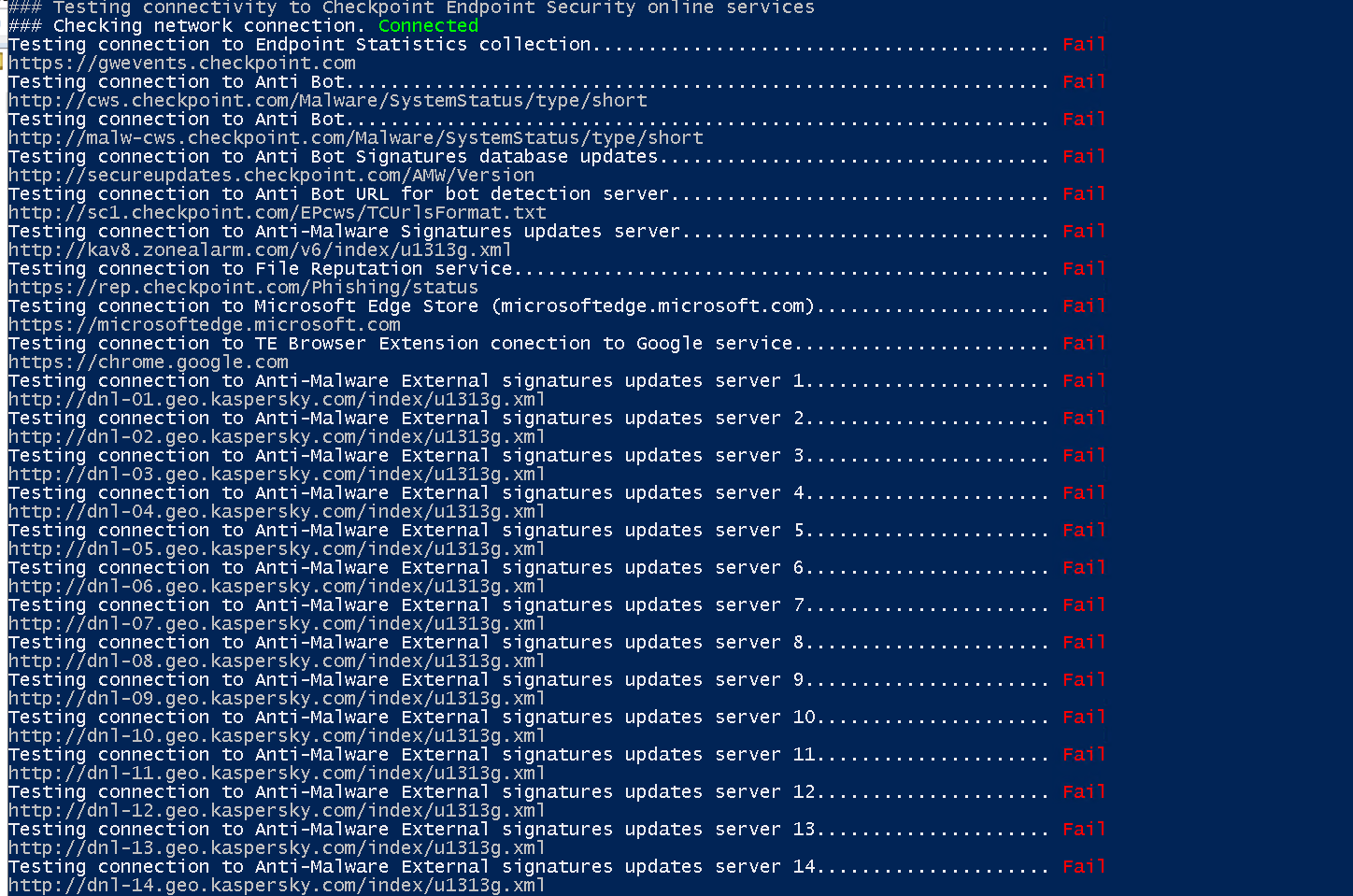
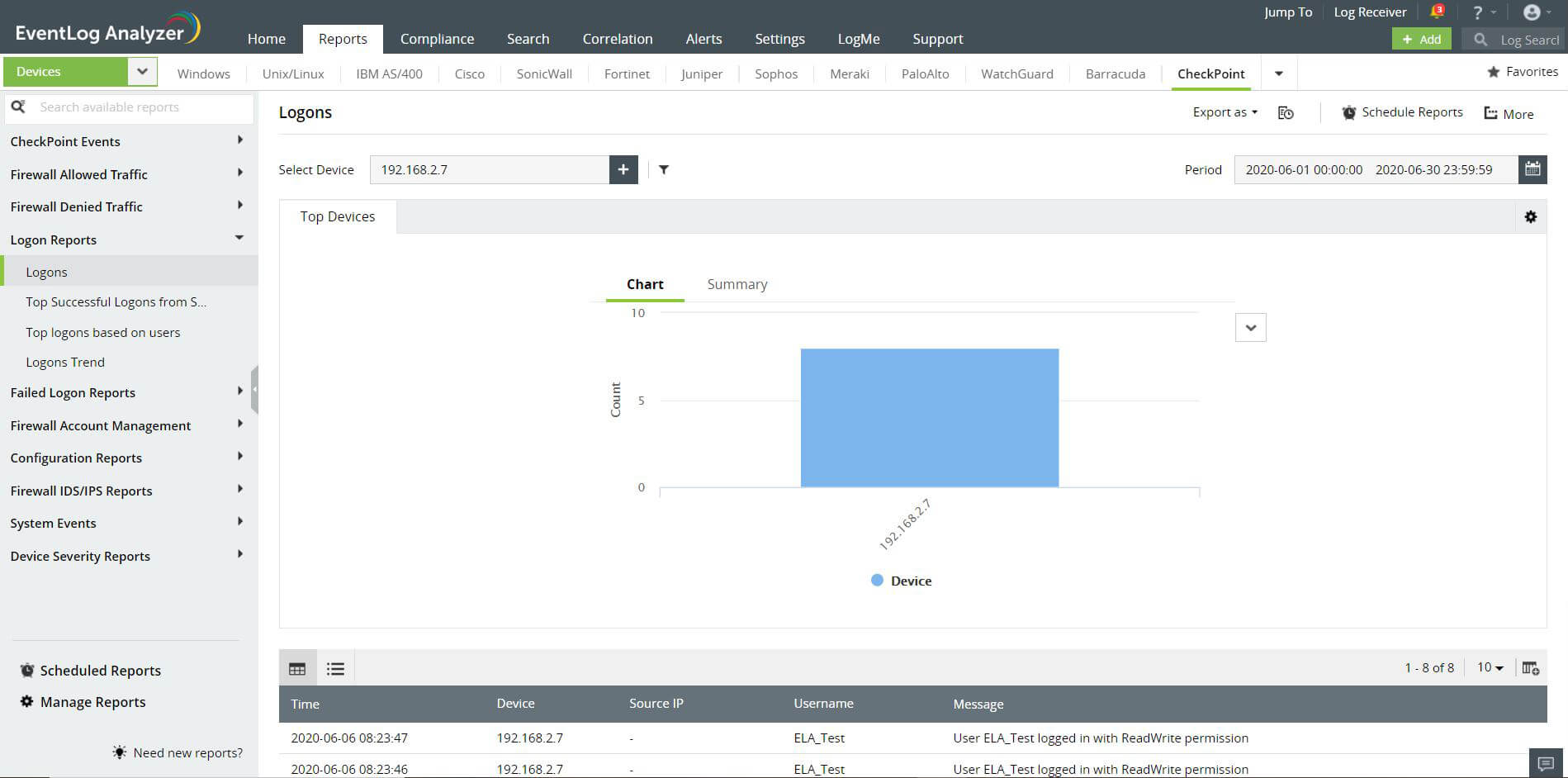
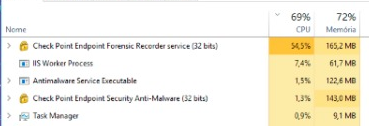
100% CPU usage when running WSL2 in Check Point Endpoint Security VPN installed environment : r/bashonubuntuonwindows
On a Windows 10 PC, how do I get rid of the check point endpoint services? If I try to stop or end the services, it just reappears. I've only recently noticed

windows - 100% CPU usage when running WSL2 in Check Point Endpoint Security VPN installed environment - Super User

US7987490B2 - System and method to acquire, aggregate, manage, and distribute media - Google Patents