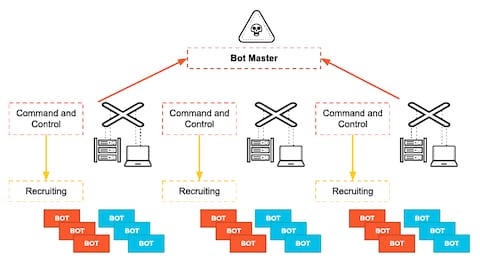
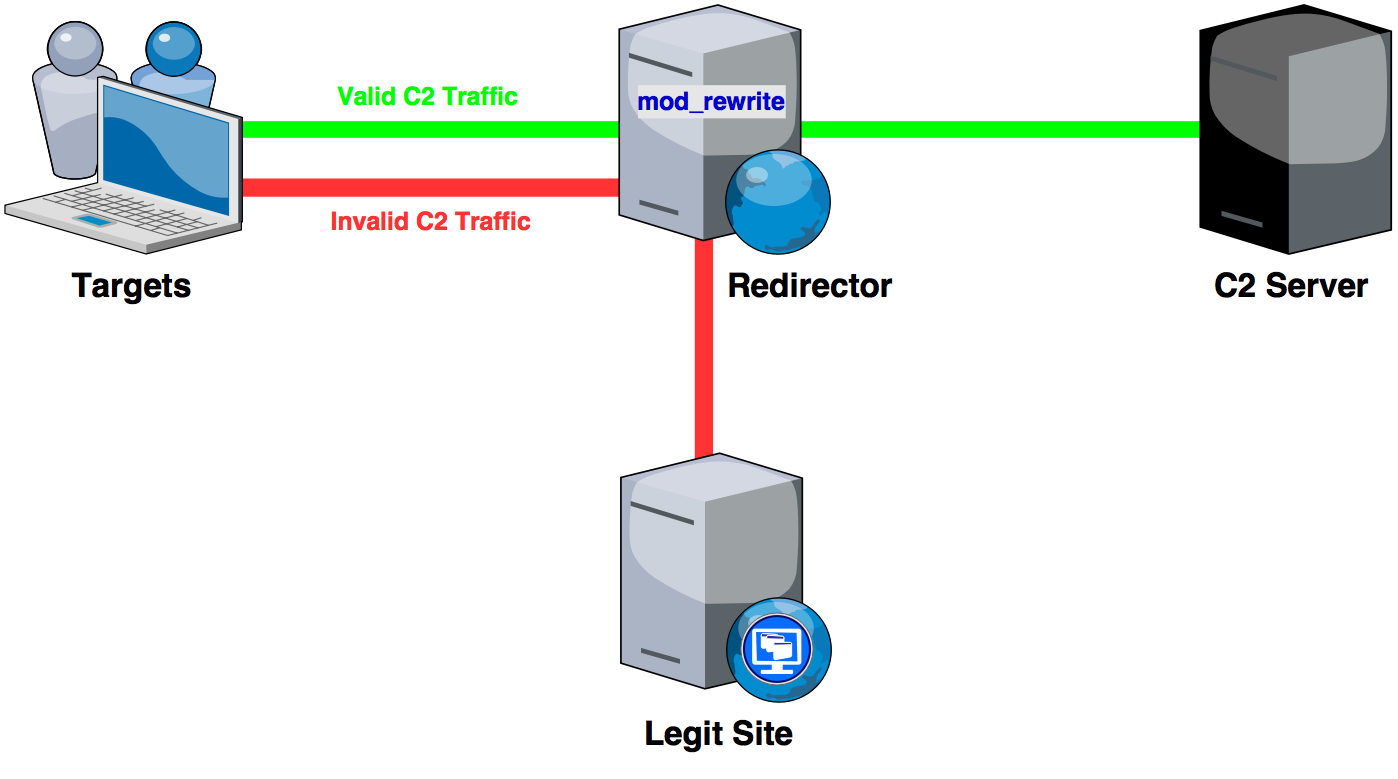
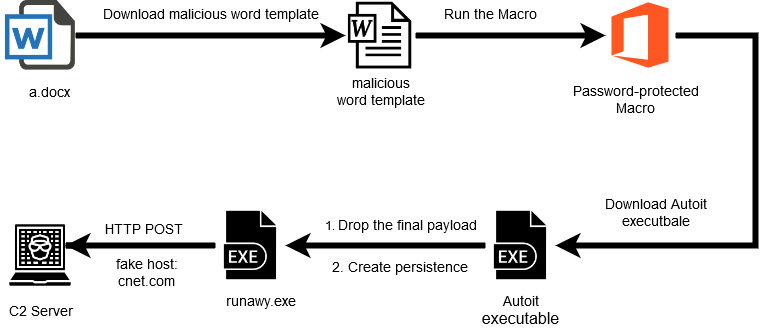
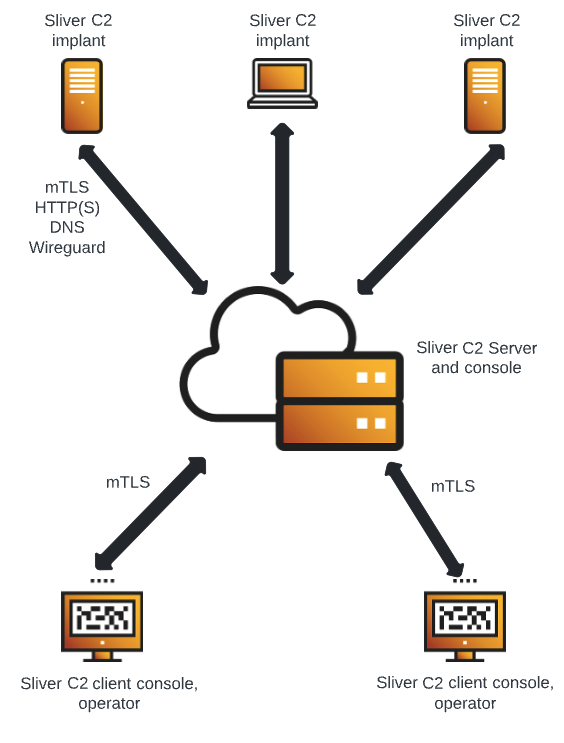
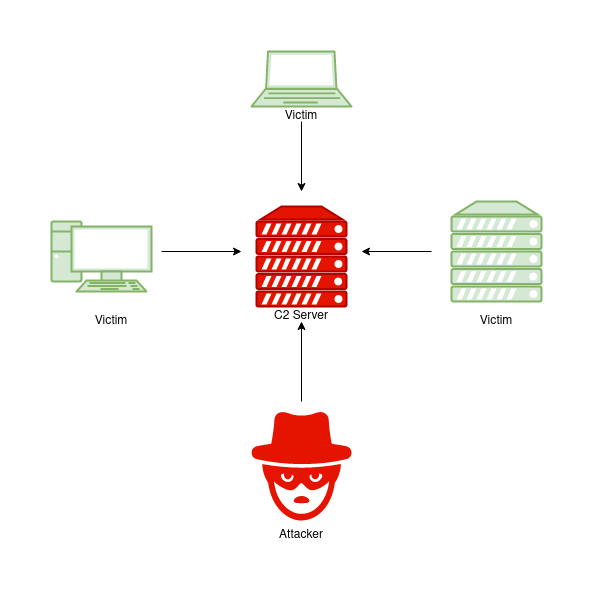
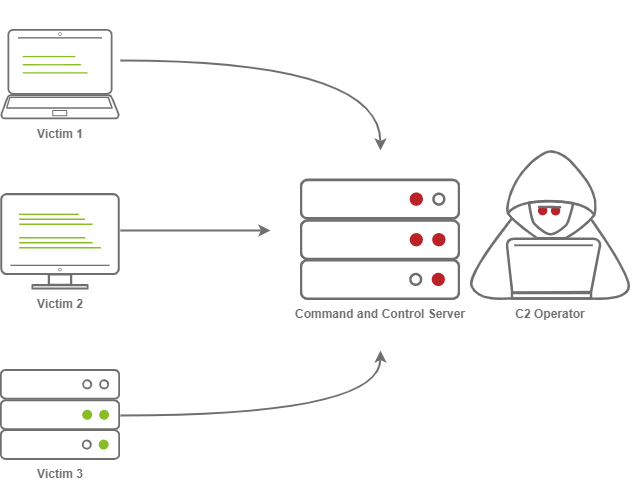
Exploring C2 Servers: Command And Control Infrastructure in Cybersecurity | by Sourabhprixitshankhyan | Medium

Active C2 Discovery Using Protocol Emulation Part1 (HYDSEVEN NetWire) - VMware Security Blog - VMware

Stopping C2 communications in human-operated ransomware through network protection | Microsoft Security Blog

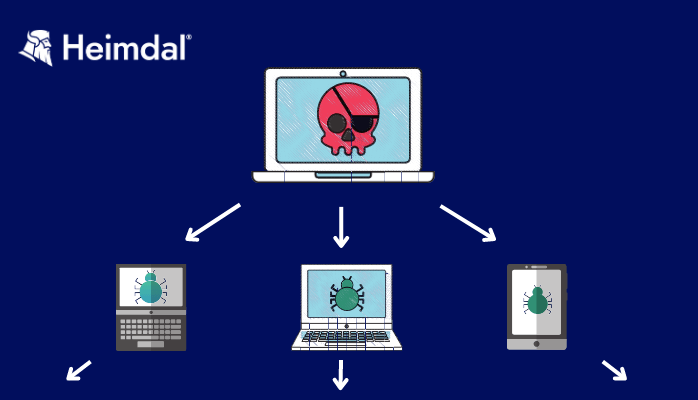

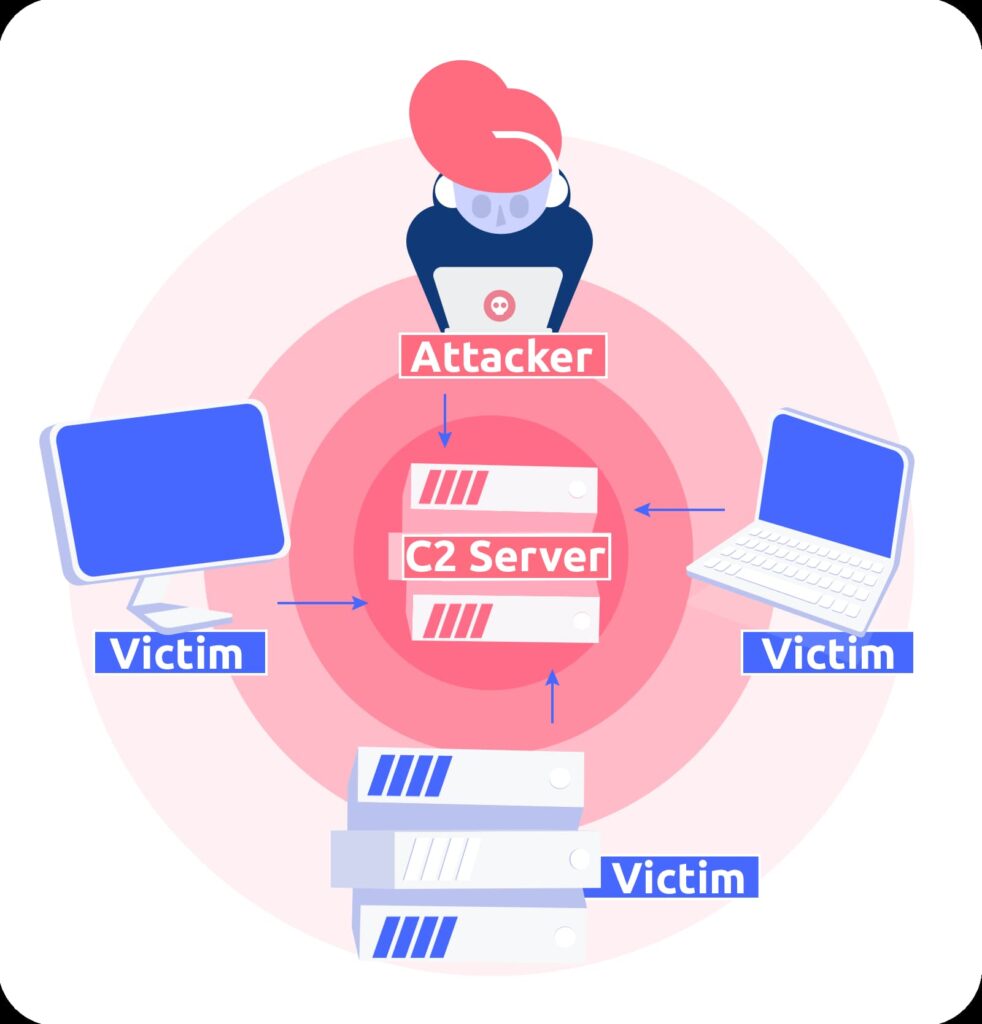
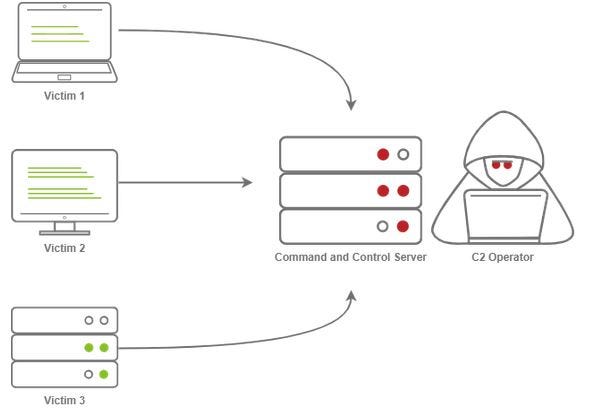


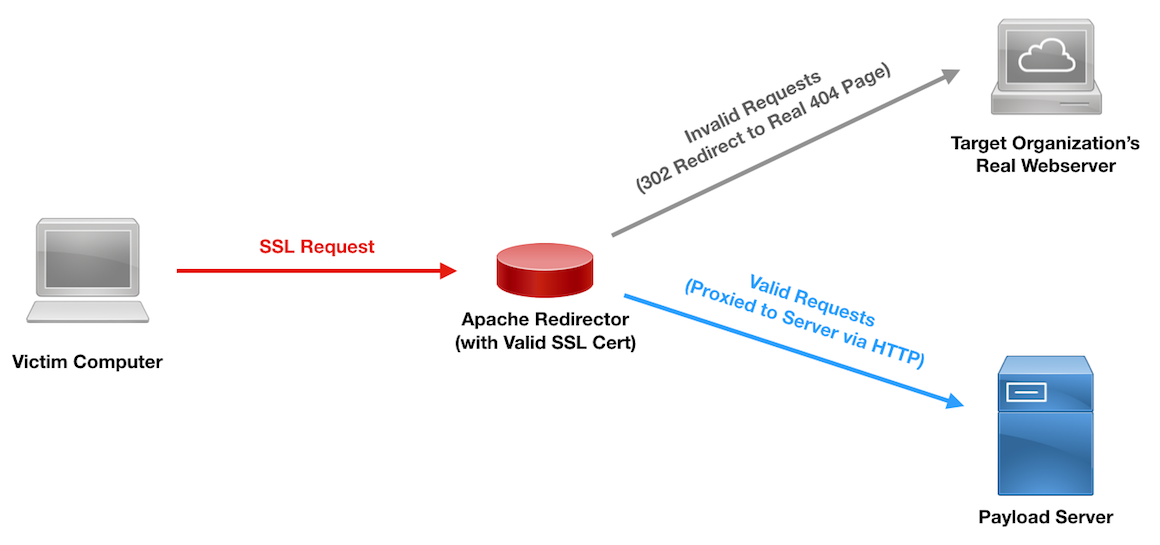





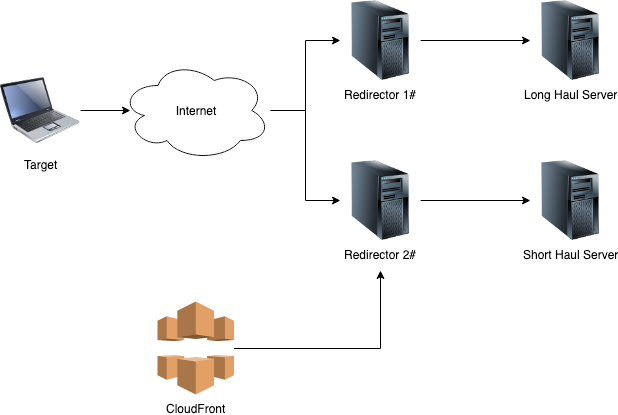
![Obfuscating Command and Control (C2) servers securely with Redirectors [Tutorial] | Packt Hub Obfuscating Command and Control (C2) servers securely with Redirectors [Tutorial] | Packt Hub](https://packt-type-cloud.s3.amazonaws.com/uploads/sites/2432/2018/12/26b0fda1-5498-470e-9257-8fab7586af4d.png)